What is HTTP?
HTTP, the Hypertext Transfer Protocol, is the ‘language’ that your web browser and websites speak to each other when you use the internet. It is mainly used to load web pages from the internet into a web browser.
The server receives the corresponding request and then sends the web page back to your browser. This is done via an HTTP response. It’s like writing a letter to someone and then receiving a reply with the information you requested.
Attacks via HTTP
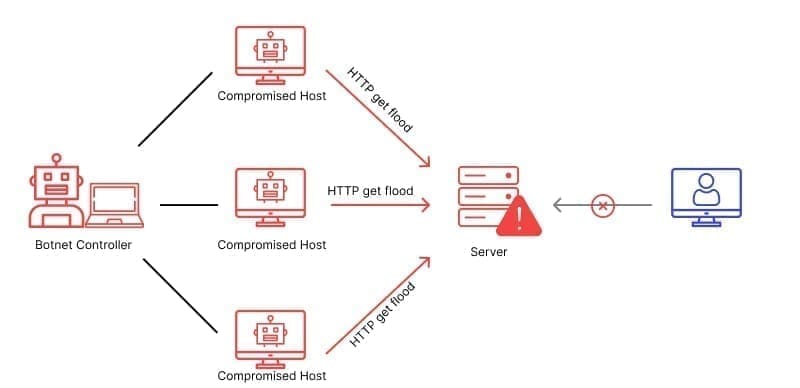
With the increasing popularity of HTTP, the security risks have increased and, like any protocol, HTTP is also vulnerable to attacks. For example, attackers use Denial of Service (DoS) attack techniques to limit the accessibility of a website. A DoS attack can be compared to flooding a mailbox with irrelevant letters so that real, relevant letters can no longer be delivered. In the world of the internet, this means that a website or online service is bombarded with so many requests that it is no longer able to process legitimate requests. As a result, the website or service is no longer available to normal users. Such an interrupted service can have serious consequences, as it denies users access to important resources or services. This can lead to a loss of revenue, especially for companies that rely on their online presence to sell products or to offer services. Furthermore, an interrupted service can affect user confidence and lead to a loss of reputation.
Connection between HTTP and TCP
HTTP runs via the Transmission Control Protocol (TCP). As a result, a web server can also be exposed to many TCP-related attacks. When planning protection for HTTP services, it is therefore important to note that the attack surface is much broader than just the HTTP protocol. Every distributed denial of service (DDoS) attack today uses multiple vectors to create a denial of service. To prevent this, the server should be able to protect itself from all these vectors. DDoS attacks are similar to DoS attacks, except that the requests are sent from different sources (vectors). A DDoS attack works similarly to mailboxes being flooded with letters. Instead of being sent by a single person, they are flooded by many different senders at the same time. These ‘letters’ are actually data packets sent to computers or websites. The large number of packets overloads the internet connection or website, making it inaccessible to normal users.
These attacks can target different services and protocols, not just HTTP. However, due to its importance to the economy and the prevalence of HTTP, the protocol is often used for DoS attacks.
What types of attacks are there?
- Injection attacks: In injection attacks, attackers insert malicious scripts or commands into HTTP requests to trigger unwanted actions on the server. For example, SQL injection attacks can be used to manipulate database queries and access confidential information.
- Cross-site scripting (XSS): XSS attacks involve injecting malicious JavaScript code into websites or web applications that are viewed by other users. This allows attackers to redirect users to fraudulent websites, steal cookies or hijack user sessions.
- Cross-site request forgery (CSRF): In CSRF attacks, a user is tricked into performing unwanted actions on a website where they are already logged in. This is often done by embedding malicious requests in legitimate HTTP requests, which are then executed without the user’s knowledge.
Methods for containing such attacks
Distinguishing HTTP flood attacks from normal traffic is very difficult because they use standard URL requests. This makes them one of the most challenging non-vulnerability-based security challenges servers and applications are facing today. Traditional rate-based detection is ineffective for HTTP flood attacks because the volume of traffic for HTTP floods is often below detection thresholds.
The most effective mitigation mechanisms rely on a combination of traffic profiling methods, including IP reputation identification, abnormal behaviour monitoring, and the use of advanced security challenges (for example, JavaScript parsing prompts).
Web Application Firewall (WAF) – a Solution for This Type of Attack
How a WAF blocks an attack from a compromised host. Image source: https://www.cloudflare.com/de-de/learning/ddos/glossary/web-application-firewall-waf/
A WAF, or ‘Web Application Firewall’, is like a security service for a website or online application. Imagine your website is a house, and the WAF is a bouncer who stands at the door and checks everyone entering to make sure they are not a threat.
If someone tries to visit your website, they have to get past the WAF. Similar to how security personnel check the identity and intentions of people, the WAF inspects the incoming traffic on your website. It checks whether the requests come from real users or whether they are malicious attacks, such as attempts to paralyse the website or access confidential data.
How Does a WAF Work?
A WAF protects your web applications by filtering, monitoring and blocking any malicious HTTP/S traffic passing through the web application and preventing unauthorised data from leaving the application. It does so by checking against a set of policies that help determine whether traffic is deemed malicious or safe. Just as a proxy server acts as an intermediary to protect a client’s identity, a WAF works similarly, but in reverse – as a reverse proxy – and acts as an intermediary that protects the web application server from a potentially malicious client.
WAF Security Models
Three security approaches are typically applied by WAFs:
- Allowlisting: A ‘permission list’ that uses machine learning and behaviour modelling algorithms to define what traffic is allowed through by the WAF. Everything else is blocked.
- Blocklisting: A ‘blocklist’ based on current signatures against known vulnerabilities that define which traffic is rejected by the WAF. Anything else is accepted.
- Hybrid approach: The WAF relies on a combination of positive and negative security models: a combination of allowlists and blocklists that determine what is allowed through.
What Are Network-Based, Host-Based and Cloud-Based WAFs?
A WAF can be implemented in one of three different ways, each of which has its own advantages and disadvantages:
- A network-based WAF is generally hardware-based. Since it is installed locally, it minimises latency, but network-based WAFs are the most expensive option and require the storage and maintenance of physical hardware.
- A host-based WAF can be fully integrated into an application’s software. This solution is less expensive than a network-based WAF and offers more customisation options. However, the drawbacks of a host-based WAF are the use of local server resources, implementation complexity and maintenance costs. These components usually require engineering time and can be costly.
- Cloud-based WAFs offer an affordable option that is very easy to implement; they typically offer a ready-made installation that is as simple as changing the DNS to redirect traffic. Cloud-based WAFs also have no or minimal initial costs, as users pay monthly or annually for security as a service. Cloud-based WAFs can also provide a solution that is continuously updated to protect against the latest threats without any additional work or costs to the user. The disadvantage of a cloud-based WAF is that users hand over responsibility to a third-party provider, so some WAF functions may lack transparency for them.
How We Protect Our Customers from HTTP and DDoS Attacks
- We offer Cloudflare as a CDN/WAF solution.
- We help compile protective measures in the event of an attack.
- If an attack is underway, we only have limited options to support the victim. We have to primarily focus on protecting other customers from the effects of the attack.
- This means that we assign data traffic to a null route so that the victim becomes unreachable. This reduces the network load, while other customers can still be reached.
Conclusion
HTTP can be subject to various attacks, such as DoS, injection, XSS, CSRF, SYN flood and GET flood. A WAF is a comprehensive solution to protect web applications from such attacks. It can be network-, host- or cloud-based. It is most important to choose the option which prepares you best for an attack, and at Nine, we are happy to help you find and implement the protective measures that are right for you.
Featured image: How the botnet controller controls compromised hosts when a server is attacked. Image source: https://www.wallarm.com/what/website-security-and-prevention-of-a-http-flood-attack