The semi-annual report recently published by MELANI (Swiss Reporting and Analysis Centre for Information Assurance) addressed several topics that are also relevant to us as a hosting provider. In this blog post, we would like to discuss some of our thoughts on this report in order to raise customer awareness for certain security issues relating to hosting.
Vulnerable content management systems
Thousands of new websites go online every day. According to current estimates, there are presently around 850 million in the world. This is mainly due to the wealth of content management systems (CMS) available, such as WordPress, Typo3, DjangoCMS and Drupal, which allow any individual, SME or web agency to create and put a website online.
As with all software, however, it is important to make sure that the CMS is always up to date and that security updates are regularly installed to safeguard websites against criminal abuse. This is even more important if the web application also uses a database containing customer information.
Web applications hosted by nine.ch periodically fall victim to hacking attacks as well. When this happens, we receive abuse reports from SWITCH, Google, Spamcop, etc. and then pass this information on to our customers. If a CMS ever becomes compromised, the clean-up process can be extremely time-consuming. The malicious files must be found and deleted, systems have to be restored from backups. In some cases this involves website downtime or – even worse – data loss.
One common reason appears to be that web applications are created, installed and then simply handed over to the customer, without any service agreement. While this may have been just fine in the past, it is no longer appropriate nowadays. This is why we advise customers working with an external partner to enter into a service agreement so that the CMS is always kept up to date. If you don’t have a partner who can manage these tasks for you, let us know. We can usually recommend a suitable partner for you.
At nine.ch, availability and competent support are the main focus, which is why our Managed line of products does not include a CMS. There are too many different CMSs on the market for us to offer the same level of expertise as our customers are accustomed to receiving from our support team. This is why we recommend working with partners who are experts in the respective CMS system. With all of this in mind, nine.ch therefore offers the following scope of service for its Managed Servers:
- nine.ch manages the server, operating system as well as Managed Services such as MySQL and Apache with PHP. nine.ch is responsible for all security updates for all components involved.
- The customer is responsible for everything that uses the Managed Services provided by nine.ch, i.e. the CMS and its applications.
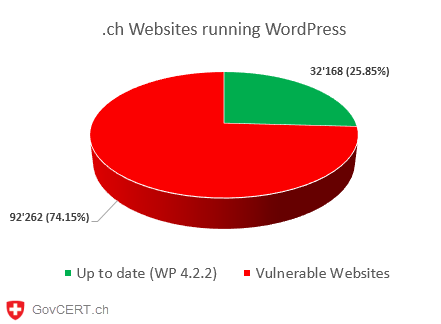
MELANI reports that more than 70% of Swiss WordPress installations are currently vulnerable. However, there are other CMSs that are also inadequately protected even though security updates are in fact available.
/vulnerable_wordpress_sites_ch.png)
Promptly installing security updates on the CMS can reduce risk, but unfortunately cannot eliminate it altogether. MELANI recommends taking the following additional precautions, which can be used with Managed Server products from nine.ch:
- restricting administrator access to certain IP addresses
- restricting administrator access using an .htaccess file on the Apache web server
- securing the webmaster computer
- promptly identifying security gaps
These and other precautions are summarized in a fact sheet from MELANI, and our support team will also be happy to advise you should you have any questions about protecting your CMS.
DDoS attacks
DDoS attacks are also mentioned in the MELANI semi-annual report. Unfortunately, nine.ch has also seen an increase in such attacks, particularly during the months of November and December.
Criminals take advantage of the fact that many online retailers record their highest sales in November and December, making them most vulnerable and receptive to potential threats during this time.
The attacks always fit a similar pattern: first, a moderate DDoS attack with a bandwidth ranging between 10 and 15 Gbit/s is launched against the respective website. The victim then receives an e-mail demanding payment, usually in Bitcoins because this digital currency is very hard to trace. If the payment is not received, the criminals threaten to launch a much larger DDoS volume of 400-500 Gbit/s. No attack of this magnitude has been documented to date, so it is unclear whether these groups are actually capable of launching one. Unfortunately, this is irrelevant because much smaller bandwidths are sufficient to take down a website.
nine.ch responds to such cases with what is known as IP blackholing, which involves rejecting the IP packages before they can be transmitted over our network. As a result, the attackers are unfortunately still able to achieve their goal of taking down the website, but at least this method prevents other servers from getting caught in the undertow.
After the unfortunate DDoS season in November and December 2014, nine.ch decided to evaluate and roll out its Managed DDoS Protection solution. We selected the market leader for this service and entered a partnership with CloudFlare. Like so many things in this world, this solution is not perfect and has certain disadvantages. In most cases, however, the benefits outweigh the drawbacks, and we can use this service to safeguard operations, even if someone decides to extort one of our customers in this way.
If you are at risk or perhaps receive an e-mail threat, always report this immediately to MELANI and contact Support to notify us of the incident. We can then work with you to determine what should be done next. Never, under any circumstances, pay the money demanded by the extortionist.
If you want to take precautions to prevent DDoS attacks because you believe your company is currently at risk or because you have already fallen prey to a DDoS attack in the past, please contact our Sales department to discuss how to proceed.
This wraps up our thoughts on the MELANI report covering the current situation in Switzerland. The report is interesting and very well written, and we highly recommend reading it here.
If you have any questions on the topic, please feel free to contact us. We will be happy to help you with any questions or concerns you may have.
Andy Liyanage works as Customer Solution Architect at nine.ch and uses his technical background to analyse and shape complex customer setups.